DU Community Help
Related: About this forumIs anyone able to open this or make sense of what it is?
The text on a google search shows up as...
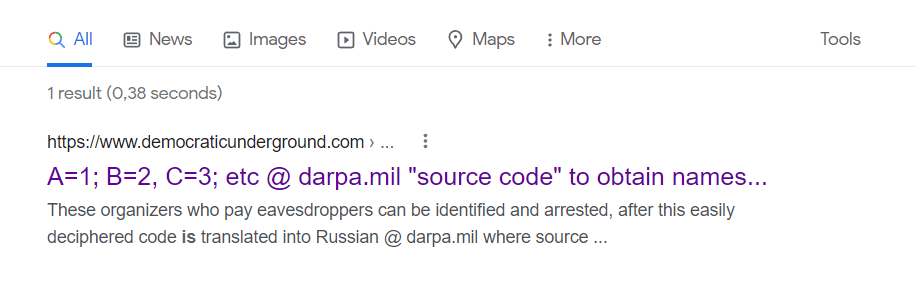
A=1; B=2, C=3; etc @ darpa.mil "source code" to obtain names...https://www.d emocraticunderground.com › ...
daily daimler daintier dainties daintiest daintily daintiness dainty daiquiri ... mail mailbag mailbags mailboat mailboats mailbox mailboxes mailed mailing
https://www.democraticunderground.com/ 10025856281 This is the link in question.
I HAVE BROKEN BOTH LINKS WITH A SPACE AS TWO REPIES HAVE WARNED OF POTENTIAL DANGER
Thanks
taxi
(2,679 posts)SmallFry
(349 posts)Thanks.
![]()
CloudWatcher
(2,127 posts)There's nothing hidden in that post. Just nonsense at the start and a long list of words.
SmallFry
(349 posts)I have a pretty solid system I work off of but the link wouldn't open for me. Just spins and spins.
CloudWatcher
(2,127 posts)The word list is 839,058 bytes. That will take a while to load, and some smaller browsers/devices might not be able to handle it well.
taxi
(2,679 posts)Glad you knew it was a joke. I was thinking about how something I'd seen earlier had reminded me of what happened with the Iranian nuclear ambitions. Poof! Immediate response!
PJMcK
(24,795 posts)Delete it.
Celerity
(53,801 posts)CloudWatcher
(2,127 posts)It's nothing.
Someone posted a 80,282 English word list (sorted).
Lists like this are often useful when trying to decode encrypted text.
The rest of the OP appears to be some ramblings of someone off their meds.
Celerity
(53,801 posts)lapfog_1
(31,707 posts)It looks like an attempt to explain a word coding system...
secure communications takes two general forms... encryption which will transmute the plain text into meaningless symbols based on sometimes rather sophisticated algorithm.
A simple (trivial) example is "rot13" where the letters of the plain text are "rotated 13 positions" such that "a" becomes "m" and "b" becomes "n" and so on.
The other method is coding... where both sides of a secure communication have a plain text to coded message dictionary so that a word like "dictionary" becomes "glop" and so on.
The problem with coding is that all possible words that may occur in the message have to be agreed upon by sender and receiver and the translation dictionary or "key" becomes a thing that must be secured.
more sophisticated coding schemes use things like a "one time pad" dictionary... where every message is encoded with a new translation.
My favorite technique is steganography... where the message (usually already encrypted using a strong algorithm ) is chopped into very small bits (in computer world, actual bits). These bits are appended to something else and are hiding in plain site. For example... lets suppose I send you a video file. In that video file format, every pixel is represented by some number of computer bits... each group of bits represents a color. Now suppose I take the least significant bit and "flip" it to represent 1 bit of the encrypted message. The video will still play... and a casual observer won't even notice any issues with the video. But if the receiver knows that the video contains a message... they can decode it by stripping the least significant bit from every pixel and then decrypting the result. A video file describes millions to billions of pixels... and so the sender can transmit very complex messages. If they also code the message then even if the intercept KNOWS that this is an encrypted stegograph, it doesn't help them understand what is being sent.
Not sure what the poster was trying to communicate with the posting.
SmallFry
(349 posts)Celerity
(53,801 posts)please delete this (locked) insane post, I am so so so sick of it showing up in DU search for years
it is a list of thousands of words
A=1; B=2, C=3; etc @ darpa.mil "source code" to obtain names...
This discussion thread was locked as off-topic by hlthe2b (a host of the General Discussion forum).
Sun Nov 23, 2014, 09:20 AM
https://www.democraticunderground.com/10025856281
advanced numerological code made easy with revised code keys...[Because FBI online agents are inefficient at code, darpa.mil offers an easy way to obtain complete information on coordinators of eavesdroppers at military bases, now that names and other information is easly revealed on these eavesdropping crime syndicate organizers. These organizers who pay eavesdroppers can be identified and arrested, after this easily deciphered code is translated into Russian @ darpa.mil where source code offered bY RUSSIAN SATELLITE TEAMS THAT KEEP THEIR BARGAINS AT ESPA CENTERS UNLIKE DOD TRAITORS @NSA.gov = Tiddosm gs;dr g;sh 1=a; 2=b; 3=c; 01=aa; 010=aaa; etc...]
a
aa
aaa
aaas
aarhus
aaron
ababa
abaci
aback
abacus
abacuses
abaft
abalone
abandon
abandoned
abandoning
abandonment
abandons
abase
abased
abasement
abases
abash
abashed
abashes
abashing
abasing
abate
abated
abatement
abater
abates
abating
abattoir
abattoirs
abbas
abbe
abbes
abbess
abbesses
abbey
abbeys
abbot
abbots
abbott
abbreviate
abbreviated
abbreviates
abbreviating
abbreviation
abbreviations
abcs
snip
it goes on and on and on and on